During times of universal deceit, telling the truth becomes a revolutionary act. – George Orwell.
SO, what is the truth about the dark shadow of doubt that continues to linger over Indian Electronic Voting Machine (EVM)—that they can be hacked or rigged to fix elections. The controversy acquires a fresh lease of life after every election in a country where the electoral machinery is in a state of perpetual motion. If the legislature, the executive and the judiciary are considered as the limbs of a well-functioning democracy, then the sanctity and fairness of the electoral process through which India elects its legislators to give itself a government “of the people, by the people, for the people” is its lifeblood. In case, this lifeblood gets contaminated by toxic pathogens such as rigging, booth capturing, ballot stuffing or hacking of EVMs leading to manipulations of votes cast, then the health of democracy is at grave peril.
Therefore, it’s pertinent to ask two questions. 1. Is it possible to hack Indian Electronic Voting Machines? 2. Have they been hacked to alter the outcome of an election? The short answer to the first question is: yes, technologically speaking, it’s possible to hack or manipulate EVMs. That’s what a number of computer scientists confirmed to gfiles, both on record and off the record.

The answer to the second question, however, is a lot more complex. We don’t know whether elections have been compromised because the Election Commission of India (ECI) has continuously stonewalled all attempts by independent computer security experts to test the machines for vulnerabilities that could be exploited to manipulate votes. It has steadfastly denied critical information that would enable people to dispel or confirm the doubts that continue to persist about the integrity of the machines. It’s for these two reasons that all political parties across the spectrum, from the left to the right, including the Bharatiya Janata Party (BJP), which is currently in power in 21 states across the country, have fanned the controversies and conspiracy theories about EVM fixing, especially after losing an election battle. In this cross-current of accusations and counter claims, the core issue of whether the EVMs are really vulnerable to manipulation tends to drift away from focus.
For the moment, the people of India have to rely on ECI’s claims that all is well and EVMs are tamper-proof despite offering no demonstrable evidence or an independent audit report to back up its assertions. Several of the claims made by the ECI in its latest Electronic Voting Machines in India: A status paper, have been questioned by computer scientists and security experts that gfiles spoke to.
The people of India have to rely on ECI’s claims that all is well and EVMs are tamper-proof despite offering no demonstrable evidence or an independent audit report to back up its assertions. Several of the claims made by the ECI in its latest Electronic Voting Machines in India: A status paper, have been questioned by computer scientists and security experts that gfiles spoke to
David D. Dill is a Professor of Computer Science at the Stanford University. He is acknowledged globally as an expert on computer security and electronic voting. He has worked for over 15 years in the US towards making election results trustworthy. He remains sceptical about ECI’s claims. “I have heard presentations from the ECI at a conference in the U.S. a few years ago and found them unconvincing,” wrote Dill in an email response to a set of question sent to him by gfiles. He goes on to offer an even stronger counter. “Claims that a machine cannot be hacked are almost always false, and often demonstrated to be false in the most embarrassing possible way,” says Dill.“People who make extraordinary claims, e.g., that a machine cannot be hacked, should be prepared to provide extraordinary evidence. Refusal to embrace independent security analysis of the machines to me is an obvious indication that the people making the claims are not as confident that those claims will hold up under scrutiny”. He goes to add: “It is common sense to be sceptical about people who make claims that they are not willing to back up, especially when the claim is implausible according to technical experts. This is especially true since older versions of the machines were examined (against the will of the authorities) and hacks were demonstrated.” It’s worth noting that till date, the ECI has failed to provide any “extraordinary evidence” to back up its “extraordinary claim” that its EVMs can’t be hacked.
Questions sent to GVL Narasimha Rao
BJP MP (Rajya Sabha) & National Spokesperson
-
- Do you still stand by the contents of Democracy At Risk, now that the BJP is in power not only at the Centre but also in 21 states?
- In 2009, when the NDA was in opposition, it accused the Congress of rigging the EVMs. Now that the BJP is in power, the opposition accuses your party of rigging EVMs. What is your and your party’s reaction about this role reversal?

- In your book you made a very serious charge that certain politicians were approached by ‘election fixers’ who offered to fix the EVMs for a price of Rs 5 crore and that these fixers were people with ‘authorised’ access to EVMs. Do you believe that such fixers are still in business or have ceased to exist with the change of party in power?
- In 2010, Hari Prasad and his team demonstrated that EVMs can be hacked without access to the source code or machine code. You have also quoted Prasad in your book. Do you think in light of the demonstration given by Prasad, there is still a case of EVM hacking?
- In 2009, Subramanian Swamy, who is now a BJP MP, filed a PIL in the Delhi HC. But after the Karnataka elections, when he was asked about Congress’s accusations of EVM hacking, he simply laughed of the accusation. What has changed?
- What is your and your party’s stand on the Election Commission of India’s consistent refusal to allow security audit of EVMs conducted by independent computer security analysts?
EVEN as India’s election body stridently refuses to entertain any request from computer security experts to test its machines, hackers at the 2017 DEFCON provided tons of demonstrable evidence that no voting machine is tamper-proof. DEFCON, established in 1993, is the world’s biggest jamboree of hackers and computer security experts that’s organised every year in Las Vegas. Last year, it drew 25,000 participants from around the world. For the first time in 2017, DEFCON set up a Voting Village with the sole purpose of allowing hackers to test the machines for security flaws and vulnerabilities that could be exploited to manipulate votes. The Voting Village put up 25 different types of voting machines, including networked and non-networked stand-alone Direct Recording Electronics (DRE) devices—similar, but not the same, to what is used in India—for security analysis by some of the sharpest minds in the world.These machines were legally sourced either from their respective manufacturers or from the open market.
On July 27, 2017, when the gates of the Voting Village were opened, complete mayhem ensued as hackers started tearing apart the hardware and the software of the voting machines. It took less than 90 minutes for the hackers to reveal some of the security flaws in the machines. Victor Gevers, a white hat hacker and founder of GDI Foundation, who has 5,392 responsible vulnerability disclosures to his credit, reported from the scene on his Twitter timeline (@0xDUDE): “You should visit the voting machine hacking village @defcon. It’s actually a horror show if you start looking at these machines up close.”
After three days of the horror show, the faith of senior officials of the Department of Homeland Security and the Department of Justice in the infallibility of the machines was firmly shaken and shattered. The extent of damage and manipulation that could be carried out was summed up in a 18-page report titled, DEFCON 25 Voting Machine Hacking Village co-authored by Matt Blaze (University of Pennsylvania), Jake Braun (University of Chicago), Harri Hursti (Nordic Innovation Labs), Joseph Lorenzo Hall (Centre for Democracy & Technology) Margret MacAlphine (Nordic Innovation Labs) and Jeff Moss (founder of DEFCON). Though, the report focused exclusively on machines used in the US, it provides enough evidence that’s equally valid to counter the claims that the ECI has routinely trotted out in defence of its machines.
Questions sent to Alex J Halderman
Professor of Computer Science and Engineering, University of Michigan
-
- As you are aware of that the Indian Supreme Court has directed the ECI to implement 100 % VVPAT. So, is it technologically possible that the VVPAT slips show the correct output, while the actual vote recorded in the memory of the machine can still be manipulated?

- Is it possible to manipulate the machine code before it’s hard coded into the one time programmable microchip even without access to the source code?
- Given that the ECI has no control over the source code, which is written by the employees of state-owned companies like the ECIL and BEL, what are the chances that unscrupulous insiders working on the code leave a backdoor open that can be exploited later?
- Is it possible to check if the machine code matches the source code after the EMV machines have been assembled? If yes, how?
“The results were sobering. By the end of the conference, every piece of equipment in the Voting Village was effectively breached in some manner. Participants with little prior knowledge and only limited tools and resources were quite capable of undermining the confidentiality, integrity, and availability of these systems,” says the report. “Moreover, a closer physical examination of the machines found, as expected, multiple cases of foreign-manufactured internal parts (including hardware developed in China), highlighting the serious possibility of supply chain vulnerabilities.” The report further states that such supply chain vulnerabilities can be exploited by anyone with mal-intent. “This discovery means that a hacker’s point-of-entry into an entire make or model of voting machine could happen well before that voting machine rolls off the production line. With an ability to infiltrate voting infrastructure at any point in the supply chain process, then the ability to synchronise and inflict large-scale damage becomes a real possibility.”
WHILE Indian EVMs, assembled by the Electronics Corporation of India Limited (ECIL) under the Department of Atomic Energy and Bharat Electronics Limited (BEL) under the Ministry of Defence, don’t use Chinese components, they do, however, use the most important component, the microchip (also called microcontroller), manufactured by Renesas Electronics, Japan, and Microchip Technology Inc., USA. Various other critical components that go into the manufacturing of EVMs are also supplied by third-party vendors, exposing them to the same supply chain vulnerabilities that the DEFCON report highlights.

INTERESTINGLY, the Indian media, barring a few tech websites, completely missed or buried the important story of EVM hacking at DEFCON which has implications over here. Even more puzzling is the reactions of celebrity editors and star journalists and anchors, often bordering on ridicule, every time allegations of EVM rigging surfaced, without offering a shred of evidence to the contrary. A few tweets by two of India’s most well-known journalists are enough to underline the cavalier attitude that pervades the Indian mediascape towards an issue of such vital importance.
“On your knees guys who’ve demonised EVMs and EC. A collective apology is needed. Whatever the result, this is no fixed election. Wonderful truth: no poll ever is in India (sic),” tweeted, Shekhar Gupta (@shekhargupta), editor-in-chief of The Print on the morning of December 18, 2017—the day the results to the Gujarat assembly elections were declared. Earlier on December 9, he tweeted, “EVMs are the loser’s fake excuse. Everybody screaming about them wasn’t complaining when they won. And they won’t when they win again. (sic)” Similarly, on March 3, the day of results to the Meghalaya, Manipur and Nagaland assembly elections were declared, Barkha Dutt (@BDUTT) wrote on her twitter timeline: “Always said EVM whining is the sign of a sore loser. Just like those channels who say ratings are rigged…except in the rare weeks they do well.” On May 28, the day of the Kairana parliamentary byelections, when news came in that Rashtriya Lok Dal chief, Ajit Singh, and Ram Gopal Yadav of Samajwadi Party sought a meeting with the Chief Election Commissioner over reports of large-scale EVM malfunctioning throughout the constituency, she attempted a mild walk back, “Have always scoffed at rigged EVM theories but today’s complaints on malfunctioning machines seem far too many to be ignored.”
In their eagerness to pin the accusations of EVM rigging on to the sore-loser complex, both Gupta and Dutt, like many other journalists, inadvertently point the finger to the elephant in the room that started it all and reaped substantial political capital from it.

Background : Rewind to 2009, a book, a hack and silence
Before delving deeper, it would be worthwhile to cast our attention towards the genesis of this pesky shadow that refuses to fade away despite the best claims made by the ECI. The seed of this controversy was sown into the fertile soil of India’s electoral politics on May 17, 2009. It’s a significant date as the election results to the 15th Lok Sabha were declared on that day.
It was a day on which the United Progressive Alliance (UPA) retained power by winning 262 seats in the lower house of the parliament with the Congress emerging as the single largest party with 206 seats, improving upon its tally of 145 seats in the 2004 general elections. It meant, India’s eternal PM-in-waiting, LK Advani’s hopes of becoming the Prime Minister were permanently dashed. By the time the tide turned in 2014, with the BJP sweeping to power, the Modi-Shah duo consigned the party patriarch to its version of the Last Chance Saloon called the Margdarshak Mandal (guidance committee), which hasn’t met even once since its formation, but that’s a different story best left for another day.

Enter GVL Narasimha Rao, a graduate from the Institute of Rural Management in Anand, Gujarat. He joined the BJP in early 2009. At that time, he was the party’s in-house psephologist. At present, he is a Rajya Sabha MP from Uttar Pradesh and is one of the national spokespersons of the party and a regular face on television debates. Even as the BJP was grappling with the electoral loss, Rao, under the banner of an NGO called Citizens for Verifiability, Transparency & Accountability in Elections (VeTA), decided to take a closer look if EVMs had any role to play in helping the UPA to retain power. In other words, Rao suspected that UPA won the 2009 general elections with the help of rigged EVMs.
The Indian media, barring a few tech websites, completely missed or buried the important story of EVM hacking at DEFCON, which has implications over here. Even more puzzling is the reactions of celebrity editors and star journalists and anchors, often bordering on ridicule, every time allegations of EVM rigging surfaced, without offering a shred of evidence to the contrary
Rao, with the backing of the BJP’s top brass, Chandrababu Naidu and the likes of India’s PIL-in-chief, Subramanian Swamy, VV Rao and a team of technical experts headed by one Hari K Prasad, managing director of NetIndia Pvt Ltd, a firm specialising in cyber security and surveillance, according to its website, embarked upon an investigation through the summer and winter of 2009. Rao put together an extremely well-structured campaign that operated at multiple levels.
 The book’s foreword was written by LK Advani endorsing the claims made by Rao. It also carried two messages: one by Chandrababu Naidu and the other by Prof. David D Dill, who has been quoted earlier in this story. When gfiles asked Dill if he still stands by with what he had written in 2010, given that the BJP’s current stand on EVM rigging has changed, he said: “I wrote the preface to Mr Rao’s book because I agreed with his arguments and because I wanted the voters of India to be able to trust their election results. I was a little cautious about that, because I did not want to appear to be endorsing Mr Rao’s politics.”
The book’s foreword was written by LK Advani endorsing the claims made by Rao. It also carried two messages: one by Chandrababu Naidu and the other by Prof. David D Dill, who has been quoted earlier in this story. When gfiles asked Dill if he still stands by with what he had written in 2010, given that the BJP’s current stand on EVM rigging has changed, he said: “I wrote the preface to Mr Rao’s book because I agreed with his arguments and because I wanted the voters of India to be able to trust their election results. I was a little cautious about that, because I did not want to appear to be endorsing Mr Rao’s politics.”
The book was launched in Delhi on February 12, 2010, by the then president of the BJP, Nitin Gadkari, in the presence of senior leaders of the party. “On the one hand, we say voting percentage should be increased and voting should be made mandatory and on the other hand, people cannot vote (due to tampering of EVMs). This is not a problem of voting alone but a problem related to Indian democracy,” said Gadkari at the launch event.
IN his book, Rao makes several startling claims, but none more than the claim that during election season “fixers”, with “authorised access” to the EVMs approach politicians with offers to rig machines in favour of a candidate or a party for money. The figure quoted in the book is Rs. 5 crore per candidate is mentioned in the chapter titled: Election Fixers Demand Hefty Sums. “The ex-MP’s son stood for the Maharashtra assembly elections recently. The ex-MP told me that they were approached by some “authorised” engineers (apparently representing one of the EVM manufacturers or their agents) who offered to manipulate election results in 50 per cent of the polling stations of his assembly constituency for the princely sum of Rs. 5 Crore. The engineers said that the candidate could choose whichever polling stations he wanted manipulated,” writes Rao, quoting one retired IAS officer, Omesh Saigal, who is described as a whistleblower. He then goes on to suggest how Hari Prasad was approached by a political party to rig EVMs. “Today, some representatives of a prominent regional party came to meet us in Hyderabad. They said that they were aware that some techies from Hyderabad or Bangalore are “fixing” elections in favour of parties and candidates. Can you do this for us?” writes Rao, quoting Prasad.
Malfunctioning EVMs and VVPAT machines
ON February 16, elections to the local body were held in Buldhana, Maharashtra. During the polling at the polling station No. 56 in Sultanpur of Lonar town when the voters pressed the button against candidate No.1 Asha Arun Zore with coconut symbol, the LED against candidate No.4 of BJP with lotus symbol would light up.
Polling was cancelled only after repeated requests by other candidates and re-polling was ordered on February 21. The information about EVM recording wrong vote was revealed by RTI activist, Anil Galgia based on a reply to his query he received from the District Collector on June 16.

The second, and more widely reported, incident took place during the crucial Kairana Lok Sabha byelections in which the joint opposition candidate Tabassum Hasan of RLD was locked in a straight fight agents Mriganka Singh of BJP. Soon after the start of the voting on May 28, Hasan’s polling against started reporting EVM malfunction from various parts of the constituency. By late afternoon Hasan claimed that in over 200 polling booths either EVMs or VVPAT machines malfunctioned. Even if the number claimed by Hasan is discounted, a ground report in Daily O confirms that there was large scale EVM or VVPAT machine failures across the constituency. The ECI initially denied reports of large scale equipment failure, but by the evening the Commission ordered re-polling in 73 booths—44 in Gangoh, 23 in Nakur, five in Shamli and one in Thana Bhavan. It’s worth noting, that the places where the re-polling was ordered have substantial Muslim population who were firmly aligned behind the joint opposition candidate.
RAO also describes in detail how in September 2009, ECI officials developed cold feet after inviting VeTA representatives including VV Rao, Swamy and Prasad to Nirvachan Sadan to demonstrate that actual EVMs could be hacked in their presence. “At a tamperbility demonstration organised in Nirvachan Sadan, the headquarters of the Election Commission, referred to in chapter 8, the Commission representatives prematurely aborted an ethical hacking effort. This incident took place on September 3, 2009 when the Commission invited the petitioners of the public interest litigation in the Supreme Court to demonstrate vulnerability of EVMs. I was present at this meeting and witnessed these developments personally,” writes Rao.
On the technical side, to validate the claims of EVM hacking, leaned heavily on the work done by Prasad and his team. They publicly demonstrated two hacks on an actual Generation 2 machine obtained from an anonymous source that was stolen from a storage facility in Mumbai under the charge of the District Election Officer. The team that hacked the EVM included, Prasad, Alex J Halderman and Dutch hacker Rop Gonggrijp. They documented the hacking process in detail in an academic paper titled: Security Analysis of India’s Electronic Voting Machines that was presented at the 17th ACM Conference on Computer and Communication Security in Chicago, Illinois on October 4, 2010.

Harlderman is Professor of Computer Science & Engineering at the University of Michigan and is a renowned figure in the world of computer security and submitted a sworn affidavit in 2016 to the Senate Intelligence Committee investigating the Russian cyber attack on the servers of the Democratic National Committee in the run-up to the US elections. Gonggrijp was the founder of Dutch hacking magazine called Hack-Tic, where he described his role as hoofdverdacht (prime suspect). He was also instrumental in the release of 39-minute documentary film called Collateral Murder in collaboration with Wikileaks that showed an attack by an US Apache helicopter on a group of unarmed people in New Baghdad in which two Reuters journalists were killed.
Laying out the scope of their work, Prasad’s team noted: “In this paper, we analyse the security of India’s EVMs and related procedural safeguards. We show that while the machines’ simplicity makes them less susceptible to some of the threats faced by DREs studied in prior work, it also subjects them to a different set of highly dangerous attacks. We demonstrate two attacks that involve physically tampering with the EVMs’ hardware. First, we show how dishonest election insiders or other criminals could alter election results by replacing parts of the machines with malicious look-alike components. Such attacks are made far simpler and cheaper by the EVMs’ minimalist design, and they could be accomplished without the involvement of any field-level poll officials. Second, we show how attackers could use portable hardware devices to extract and alter the vote records stored in the machines’ memory, allowing them to change election outcomes and violate ballot secrecy.” According to computer security experts the two possible lines of attacks described in the paper can be deployed to manipulate votes even in the current Generation 3 M3 machines that have been used since 2013.

The experts also pointed out that the malicious display attack that the paper outlines in detail can still be used in the Generation 3 M3 machines. It involves replacing the original 7-segment LED display on the Controller Unit (CU) with a look-alike display that has a tiny microprocessor, a very small chip antenna and a Bluetooth module during routine serving and maintenance before the EVMs are deployed in the field. Prasad and his team demonstrated how easy it’s to conceal these components in the dishonest display. The low-cost components needed to assemble a dishonest display are freely available in the open market.
EXPLAINING how the dishonest display method can be used to steal votes, the authors write: “We also developed a more robust signalling method based on the Bluetooth RFCOMM (Radio Frequency Communication) protocol, which provides a reliable stream of communication similar to TCP. Our prototype implementation consists of an application running on an Android phone. It sends a short message to the dishonest display via RFCOMM indicating the favoured candidate and the proportion of votes to grant that candidate.
The application verifies success by waiting for an acknowledgment from the dishonest display. Our application does not use any special Android features, so it could be ported to any smartphone platform that supports RFCOMM, such as the iPhone or Windows Mobile.”
The vote stealing algorithm ensures that votes are not stolen from a candidate below a certain threshold that’s determined by the software without altering the overall total number of votes stored in the CU. “For each non-favoured candidate, it calculates the maximum votes that can be stolen given the overall vote total, the totals outputted so far, and the need to reserve a certain number of votes for the remaining candidates to prevent them from falling below the minimum vote threshold,” the authors wrote in the paper. Experts consulted by gfiles say that this is a very effective line of attack because it can be deployed at the counting stage instead on the polling day.

Prasad and his team demonstrated another method through which votes can be stolen using a clip-on memory manipulator that can be attached to the Electrically Erasable Programmable Read Only Memory (EEPROM) that stores the polling data. Though, this device is equally effective in stealing votes from one candidate to another, it’s easier to detect due it size. Therefore, experts believe that this method is unlikely to be used to steal votes.
In April 2010, Prasad demonstrated both the hacking methods on Telugu television channel TV9. After keeping quiet for months, the ECI finally filed an FIR through its Mumbai District Election Officer that led to the arrest of Prasad on August 24, 2010, for unauthorised possession of an EVM. But five days later, on August 29, he was granted bail a Metropolitan court. “No offence was disclosed with Hari Prasad’s arrest and even if it was assumed that EVM was stolen it appears that there was no dishonest intention on his part….he was trying to show how EVM machines can be tampered with,” observed Metropolitan Magistrate, VB Srikhande. Two days later, Prasad was on his way to Chicago to present the paper.
Curiously, since his release, and more so after the 2014 elections that brought the BJP to power, all the main protagonists involved with the campaign have either have kept a very low profile or maintained stony silence on the issue. There was no response to the questionnaires sent by gfiles to Rao, Prasad and Halderman, asking them if they still backed their claims made in the book or their findings published in the paper apart from other related questions (see box). The emails to Rao and Halderman were followed up by phone calls and messages on Whatsapp and Telegram but did not elicit any response from any one of them. Only, Dill responded to the email.
Fast forward : Of VVPATs and Codes
In the more recent past, two incidents—vote switching in one polling station in the Buldhana local body elections and large-scale failure of EVMs and VVPAT machines in the Kairana byelections—probably played a role in hardening of the opposition’s demand for going back to ballot paper for the 2019 general elections. (see box for details). On May 29, the ECI issued one of the most bizarre press releases regarding the Kairana incident, which didn’t help to cover itself in any glory. “During the bye-elections to 2-Kairana and 11-Bhandara-Gondiya parliamentary constituencies on 28th May 2018 malfunctioning of a few VVPAT machines was reported during mock poll and actual poll….The preliminary fact finding reports submitted to the Commission, have indicated that there were two major technical reasons for malfunction as follows: 1. Failure of contrast sensor (error 2.2) 2. Failure of length sensor (error 2.4). The above errors are mainly caused by excessive exposure to illumination in polling stations. (sic)”
The ECI’s press release is troubling on many counts. What it termed as a “few VVPAT machines” actually turned out to 384 VVPAT machines out of the approximately 1,483 deployed across the constituency according to a Daily O spot report. Also, the release was conspicuously silent about EVM failures. Experts have questioned the “excessive exposure to illumination” theory because polling booths are usually set up inside government buildings and schools, which are known to be poorly lit. Anyway, we have no idea how much illumination can be termed as excessive illumination according to ECI’s standards.
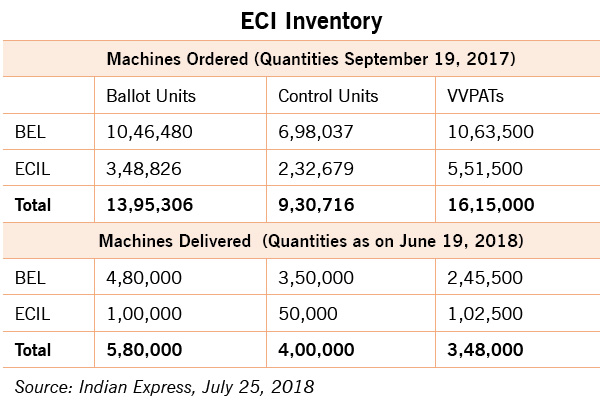
In October 2013, Supreme Court passed an order after hearing two petitions – Civil Appeal No. 9093 of 2013 and WP (C) No. 406 of 2012 the latter filed by VV Rao—that made 100 per cent implementation of VVPAT mandatory. “The confidence of the voters in the EVMs can be achieved only with the introduction of the “paper trail”. EVMs with VVPAT system ensure the accuracy of the voting system,” observed the apex court. Bound by the court order, the 2019 general elections have to be conducted with 100 percent VVPAT coverage. But a news report carried in the July 25 edition of the Indian Express, based on information accessed under RTI, shows that the ECIL and BEL are lagging way behind on the delivery schedule of VVPATs. As on June 17, the two public sector undertaking delivered just 3.48 lakh units against a total order 16.15 lakh units that would be required for countrywide deployment ahead of the September deadline. Since the publication of the report, the Commission has extended the deadline to November 2018 (See table: ECI Inventory).
However, the way the Commission uses VVPAT to audit EVM votes itself is bothersome. At present it audits the paper trail in just one polling station in each of the assembly constituency. Statistically speaking, this is against all established and accepted norms of random sampling. As pointed out in a petition filed by former IAS officer turned activist, MG Devasahayam, through an NGO called Forum for Electoral Integrity (published in the May issue of gfiles), this mandatory count of VVPAT slips in just one polling station per assembly constituency turned out to be a mere 0.4 per cent in Gujarat and 0.9 per cent in Himachal Pradesh assembly elections. This fails to pass even the most basic test of random sampling that can be statistically validated and defeats the very purpose of implementing VVPAT. In the petition submitted to CEC, OP Rawat on April 10, 2018, it demanded “that VVPAT slips must be counted for a sample size of at least 25 per cent of polling stations in an assembly constituency with the sample drawn randomly from the different strata and verified with the electronic count.”
THAT’S not all. The cornerstone of ECI’s defence of its machines is its faith in the source code and the machines code that is compiled from it. In the status paper, the Commission claims that the source code has been developed by a small group of engineers working for the two PSUs. It says that ECIL and BEL exercise complete control over it and the Commission itself doesn’t have access to the original source code. This was confirmed by the ECI in response to a set of 11 questions submitted by Mumbai-based businessman turned RTI activist, Sunil Ahya. His request included: checksum of the executable binary file (machine code) that is burnt into each programmable device, a copy of the firmware source code and copy of the procedure whereby the checksum of the executable binary file which has been burnt into each programmable device (integrated circuit) used in both the units can be audited (verified) at random at any given point in time on any of the field deployed units. The ECI’s response to these questions was, “This information is not available in the Commission (sic).”
The ECI’s defence rests on the grossly misplaced assumption that the source code cannot be decompiled from the machine code that has been burnt into the One Time Programmable Read Only Memory (OTP ROM). In fact this is a completely misleading claim. To prove that this claim is misleading we need to refer to a judgement that was delivered by the United States Court of Appeals, Ninth Circuit in the case of Syntek Semiconductor Co., Limited (Taiwan) versus Microchip Technology Inc., (USA) in April 2002.
It’s a set of specific instructions based on logic tree that helps a programme to perform specific tasks in the most efficient way. For example, when a software is optimised for better performance, it means that it is using more efficient algorithms to complete a specific task.
Checksum
It a value used to check integrity of a file or data after it has been transferred from one source to another. It is used to compare and validate two data sets to ensure they are the same on two different devices. Therefore, checksum can be defined as a unique digital signature of a data set. It can be generated by running certain specific algorithms.
Machine Code (Binary code)
For a computer to execute any programme, the source code needs to be converted into single bits of information. This is done by using Boolean logic that breaks down every letter, image or number into a base combination of 0s and 1s. This combination of 0s and 1s enable a computer to execute the set of instructions written in the source code. Programmers use a compiler to convert source code into machine code.
Microprocessor (microcontroller)
It’s an integrated circuit (IC) that is the Central Processing Unit (CPU) of a device and it processes inputs that it receives from an input device, which is converted to binary code. After processing the input, it produces an output that is written by the software.
Source Code
All computer programmes have to written in a programming language such as C, C++, Java etc. It consists of a series of instructions that’s written in a highly structured manner using words and numbers in a text file. These instructions can range from a few lines for simple programmes or millions of lines for complex ones.
In the law suit, Syntek challenged the copyright held by Microchip for the machine code that was written in the widely-used microprocessor PIC 16C5X that was manufactured by the US company because the Taiwanese company was also manufacturing a similar chip. Microchip Inc., is the same company that supplies the microcontroller that is used in Indian EVMs. The US court upheld the challenge of Syntek. And the reason why the court ruled in favour of the Taiwanese manufacturers is buried in the eighth paragraph of its order.
“Microchip did not have in its possession the original PIC 16C5x source code when it registered its program with the Copyright Office; so Microchip deposited source code that it had decompiled from the object code embedded in the PIC 16C5x computer chip. Microchip informed the Copyright Office of the nature of its deposit, stating that “[t]he source code listing provided is a listing which was regenerated from the object code of the work because Applicant could not, after a reasonable search, find a listing of the source code of the work,” says the order (emphasis added).
THEREFORE, there is no truth in ECI’s claim that the source code cannot be illegally obtained from the machine code by an insider either working for any of the two Indian public sector undertakings or working for the chipmakers in Japan and the US. For this reason, Ahya’s request for the checksum to the binary code that is hard coded into the microcontrollers assumes significance. Simply put, checksum is a sort of unique digital signature for a single piece data or code or a programme. It is generated by running an algorithm called cryptographic hash function. By comparing the checksum of a code that’s burnt into a microprocessor with the checksum of the original binary code (machine code) one can determine the integrity of the software running on the device.
In response to Ahya’s request for checksum, the Public Information Officers of BEL and ECIL took recourse to Section 8 (1) (d) of the RTI Act, which allows exemption from divulging information on account of commercial implications. In other words, the two PSUs felt that by divulging the checksum of their machine code could lead to commercial loss. Ahya challenged this during a hearing of his appeal conducted by the Chief Information Commissioner (CIC) on June 27, by saying that both BEL and ECIL can patent their codes and release the checksums.
The CIC upheld Ahya’s challenge and posted the matter for further hearing in September but not before observing that, “the commission is of the view that the defense taken by the respondents that the information is exempted under Section 8 (1)(d) has not been justified by them keeping in view that they are the only manufacturers of EVMs.” It further noted that, “the CPIOs of BEL and ECIL are directed to submit their written submission elaborating that how their competitive position will be affected if the information is disclosed. The reply should have the concurrence of CMD of the concerned public authority.”

A top computer security expert who has worked on a number sensitive government projects and does not wish to be named said, “After seeing the ECI response to the latest RTI and observing its pattern of obscurantism to attempts of scrutinising the EVMs independently, it’s clear that somewhere deep down they don’t have confidence in their machines. If they are so confident about their unhackbility then they should send a machine to DEFCON for testing.” Last year, the ECI issued a much-hyped EVM challenge inviting representatives of political parties to demonstrate the hacks. But the conditions that they attached caused much amusement in the computer security community. “They were laughable. For example, one of the terms was attempting to hack using a combination of five buttons out of the 16 on the ballot unit. The total time given was four hours. Now a simple calculation would show that using a combination of five buttons works out to 10,48,576 combinations! It would take a few months to work out those combinations. It’s clear that they have no idea how computer security or hacking works,” says the expert.
From the month long research that gfiles undertook for this story, few things are clear:
- That the EVMs are hackable.
- As long as the ECI doesn’t embrace independent computer security experts drawn from outside the PSUs, doubts will continue to persist about the integrity of the machines.
- VVPAT can erase some doubts about EVM rigging, but for that at least 25 per cent of electronic votes should be tallied against the paper trail for each assembly constituency.
- Going back to paper ballot is not an option because of our past experiences of ballot box stuffing and booth capturing.
Unlike, other Indian media houses, gfiles will be staying on this story in the months ahead and will report as and when there are any further developments.
Journalist | Editor | Allahabadi













































